The Backstory: A Friendly Challenge
At the start of 2024, after months of focused study and hands-on labs, my roommates, Mr. X and Mr. Y, frequently saw me glued to my computer, working on something mysterious. Curious, they eventually asked what I was up to. I explained my passion for ethical hacking and my need for practical, real-world testing environments to apply my skills.
Amused and intrigued, they threw down a challenge: "Why not try to hack us?" What started as a friendly joke quickly turned into a serious project. Both Mr. X and Mr. Y gave me explicit permission to test their devices and systems however I saw fit, and so, my project "You Have Been Hacked" was born.
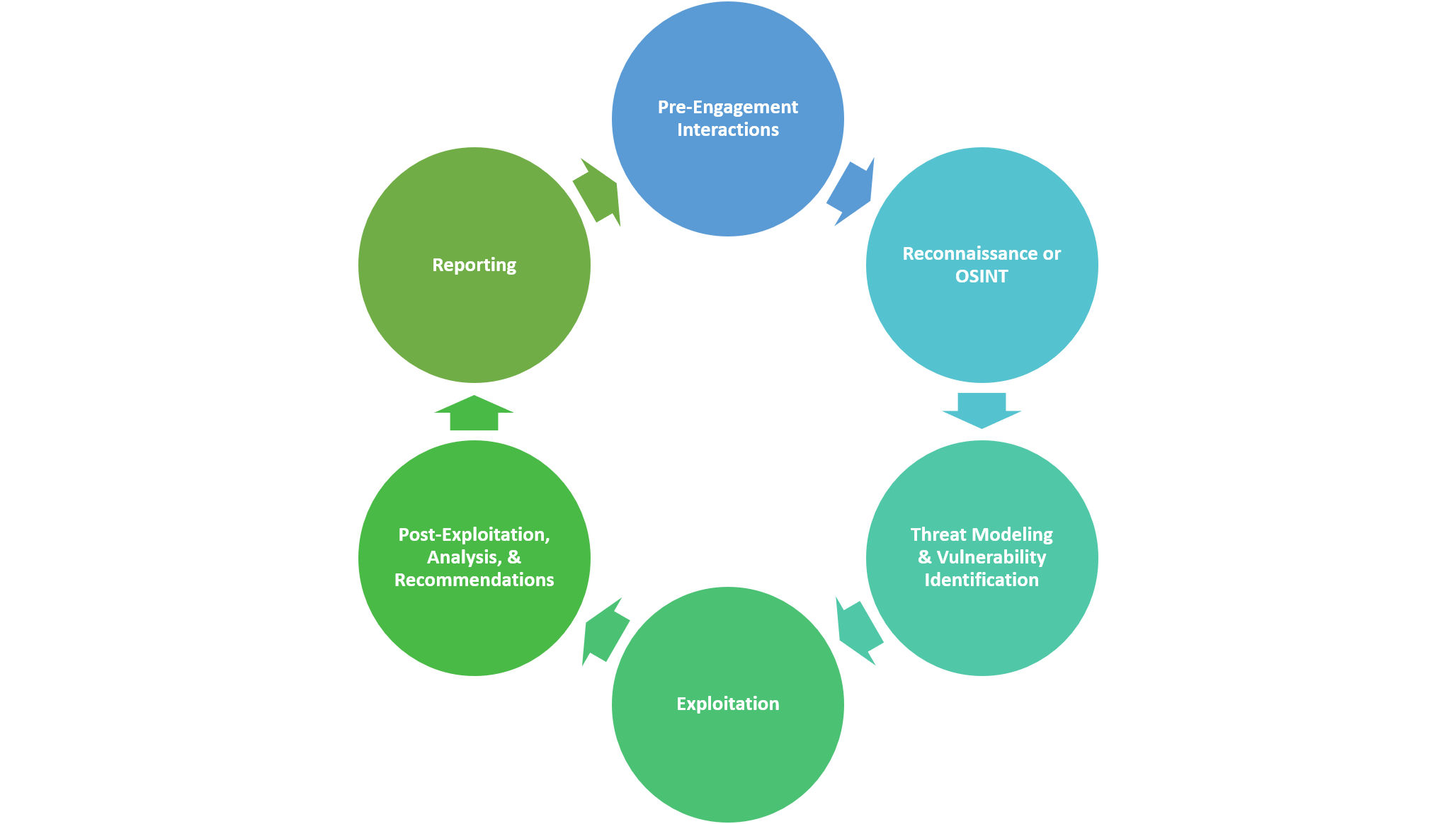
Motodology & Approach
As a beginner in practical pentesting, I decided to follow the standard phases of penetration testing. I wanted to be patient and meticulous, so I allowed a few months to pass, during which I quietly observed and collected data.
Step 1 : Reconnaissance
The first step? Reconnaissance—gathering as much information as possible about my targets, Mr. X and Mr. Y.

Target Identification: Facebook vs. TikTok
Through my initial reconnaissance, I realized that Mr. X was highly attached to his Facebook account, while Mr. Y didn’t have Facebook but spent nearly all his time on TikTok.
It became clear that I would need to split my objectives: hack Mr. X’s Facebook account and Mr. Y’s TikTok account. These two different targets allowed me to diversify my approach and test different techniques.
Behavioral insights : Facebook for Mr. X, TikTok for Mr. Y
"I will share this report with you with dated captures to have more clarity."

Data Collection: Social Engineering Setup
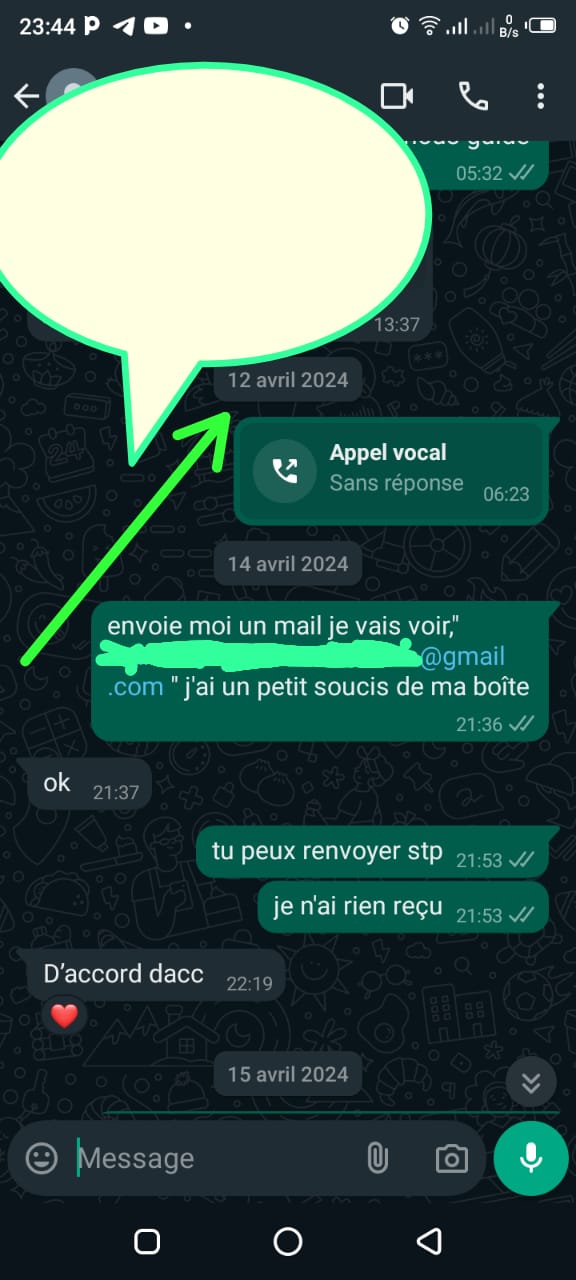
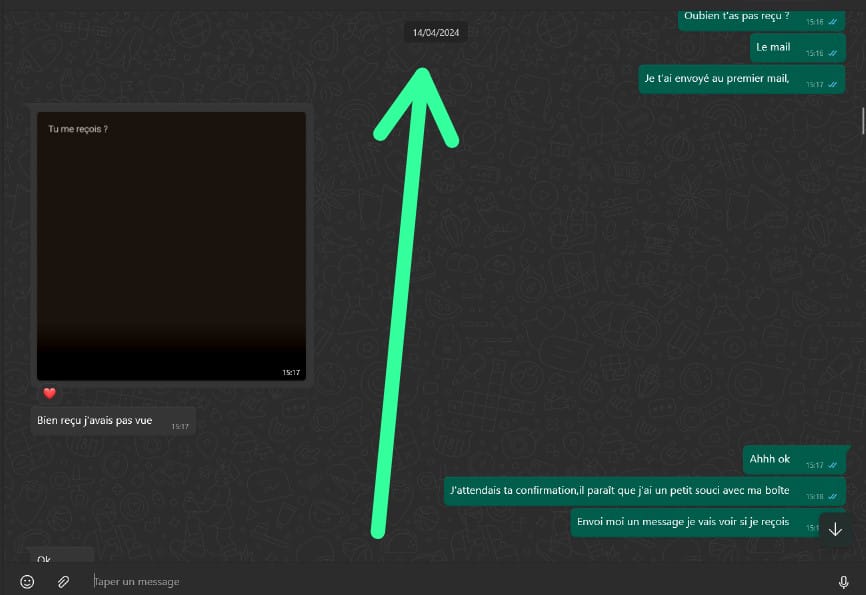
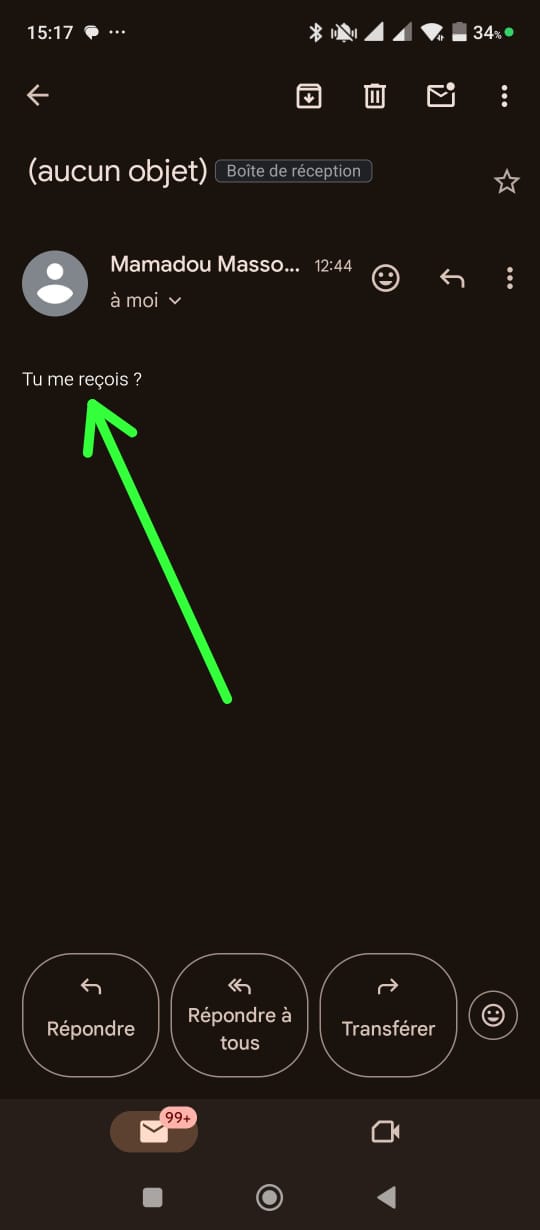
I decided phishing would be the ideal strategy. The first step was obtaining their email addresses. I asked them to share their emails with me under the pretense of forwarding an important university announcement. The trick worked, and they shared their emails without suspicion.
After sending them the legitimate university email, I crafted phishing emails that impersonated the security services of Facebook and TikTok. These emails were designed to trick them into entering their login credentials.
Collected Data : Emails gathered via a social engineering trick (WhatsApp messages)
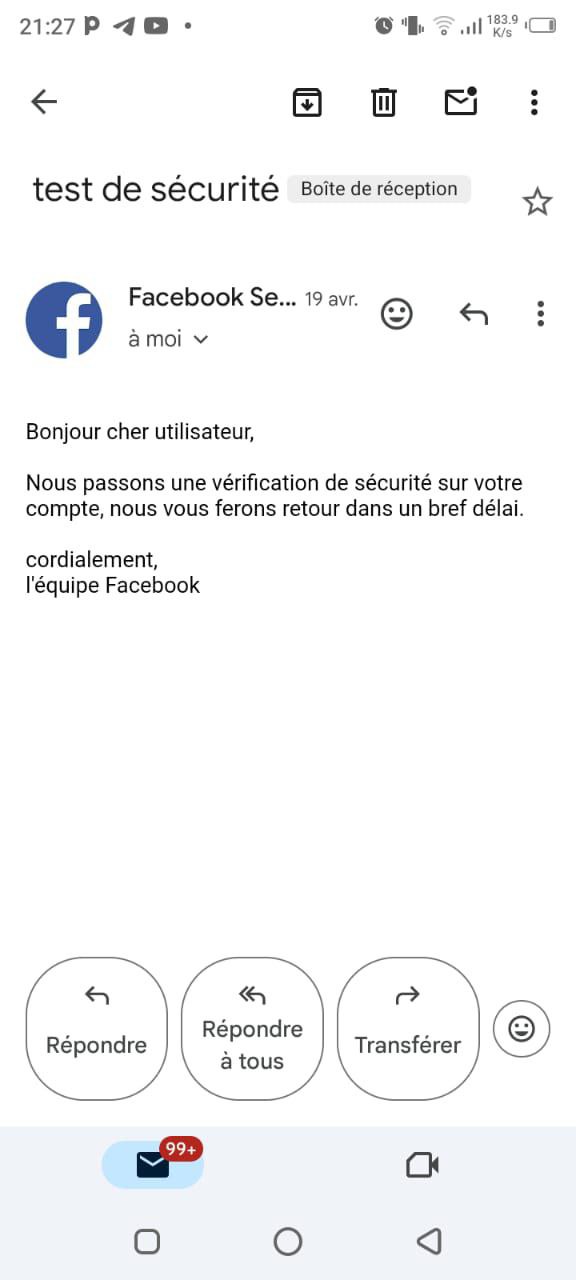
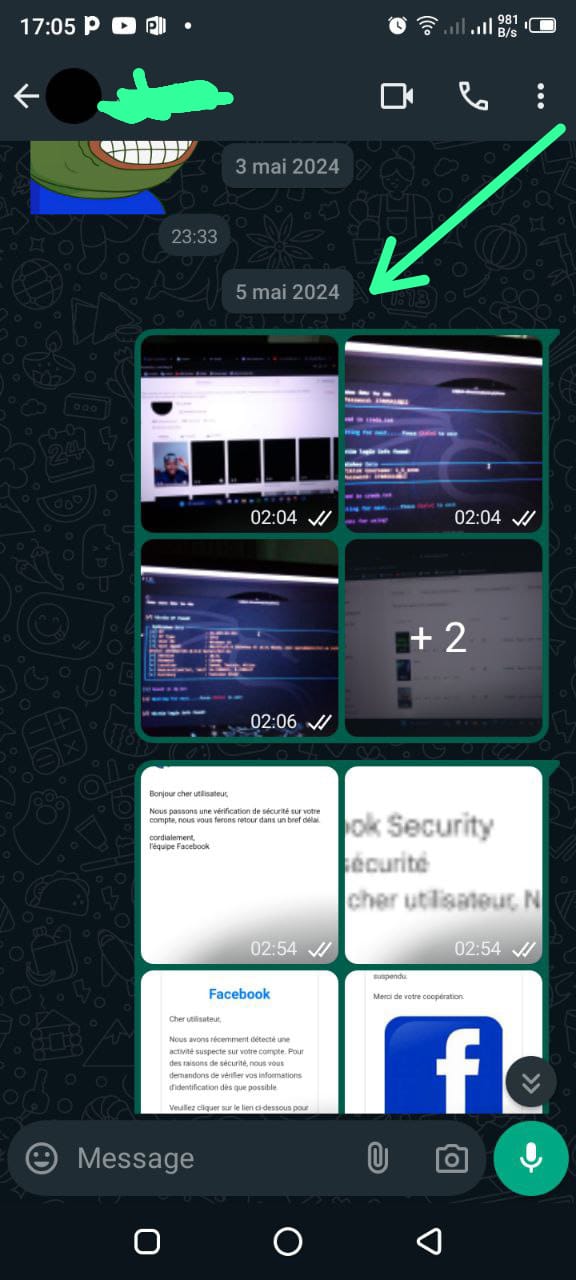
Screenshots Below : Requests For Their Emails

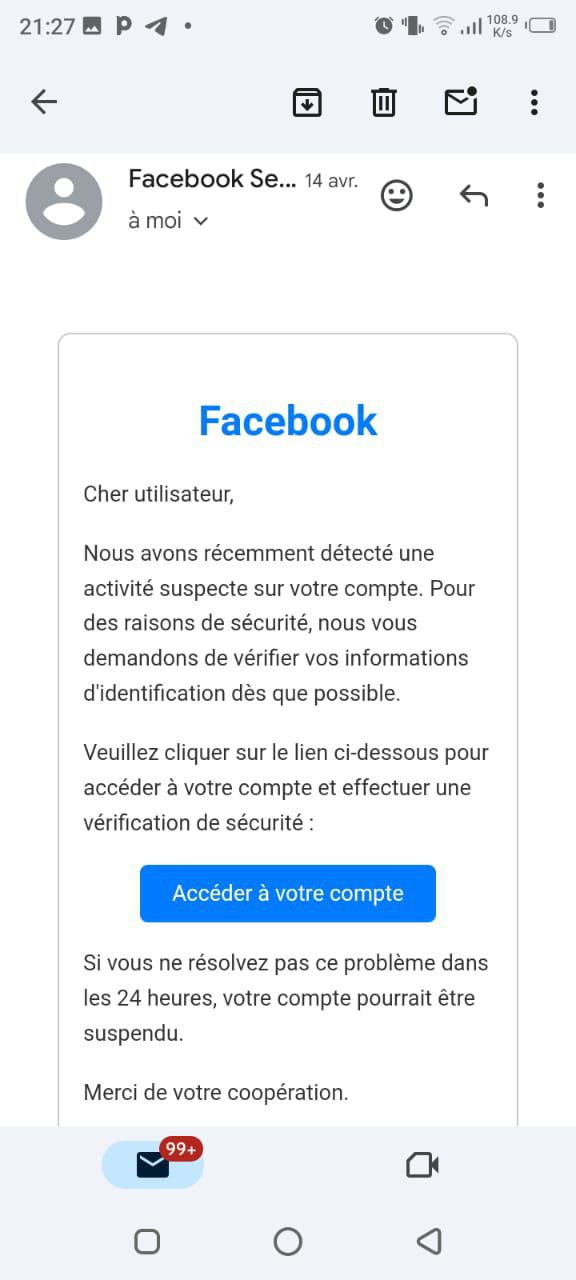
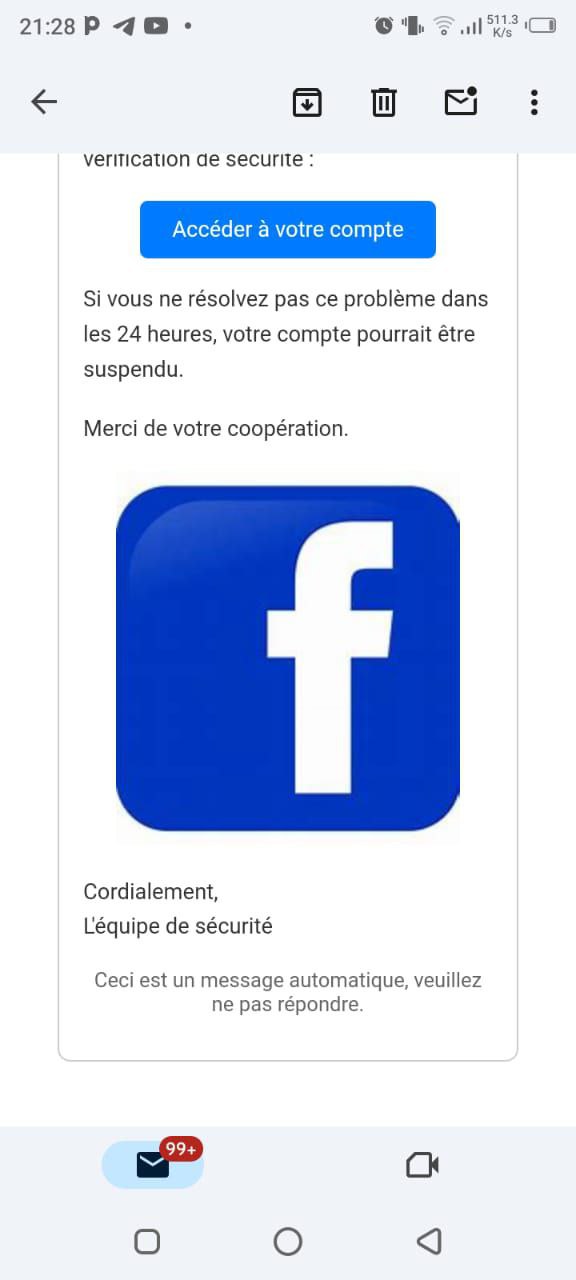
Screenshots Below : The Facebook Phishing Template
Step 2 : Scanning and Enumeration
With their emails in hand, I moved to the second phase: Scanning and Enumeration. I needed to confirm that the phishing emails I sent would successfully capture their login details when they clicked the links.
Challenges Faced : I learned quickly that Mr. X and Mr. Y were not frequent email users, which posed an unexpected obstacle. They rarely checked their inboxes, and my initial phishing attempt stalled. It became clear that this method alone wouldn’t work, I had to be flexible and adapt my approach.
Adapted Strategy : To counter this setback, I decided to be more direct. Instead of relying on email, I sent them WhatsApp messages containing the same malicious links that led to the phishing pages I had set up. On the back end, my server was already running, ready to capture their login credentials as soon as they entered them. The stage was set for the next phase.
Step 3 : Gaining Access (Exploitation)
At this point, I was ready to move to the Gaining Access phase. My phishing links were in place, my server was prepared, and now it was a matter of exploiting the human and system vulnerabilities of my targets. With a combination of social engineering and system weaknesses, I moved forward with the attack.
Vulnerability Overview:
1 - Human Factor: Both Mr. X and Mr. Y lacked awareness of phishing schemes and basic cybersecurity best practices, which made them more susceptible to social engineering.
2 - System Flaw: The browsers they were using failed to detect the malicious links, which allowed my phishing pages to bypass built-in security mechanisms.
3 - Absence of 2FA: One key insight that drove my success was that neither Mr. X nor Mr. Y had activated two-factor authentication (2FA) on their accounts, which would have added an extra layer of protection and potentially thwarted my attack.

Exploitation of Mr. X (Facebook)
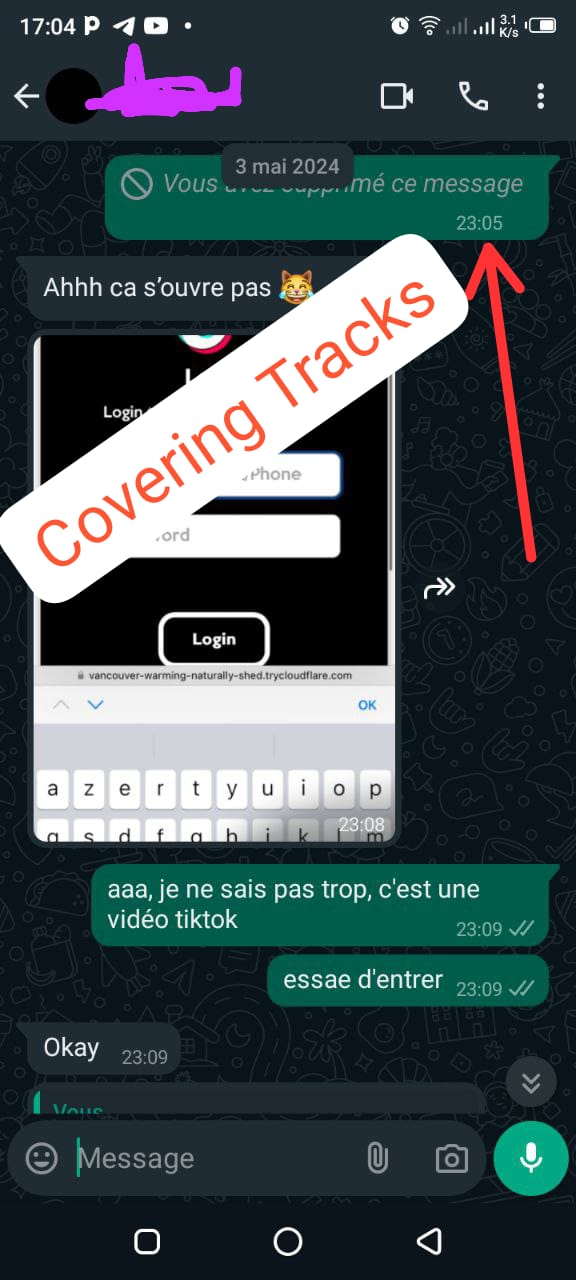
Mr. X was deeply attached to his Facebook account, so I knew targeting that would yield the best results. I crafted a convincing fake Facebook login page designed to look exactly like the real one, and I sent him a WhatsApp message with a malicious link. The message was cleverly disguised, with the link claiming to lead to a helpful Facebook video on saving battery life, something that would appeal to Mr. X.
Once he clicked the link, he was redirected to the fake login page, where he unknowingly entered his credentials. From there, my server intercepted his login information and immediately redirected him to the real Facebook video, making the entire experience seamless from his perspective. He had no idea he had been phished.

Exploitation of Mr. Y (TikTok)
Mr. Y was more skeptical, frequently boasting that I would never be able to hack him because of his "high-end iPhone." I couldn’t help but laugh every time he made this claim, knowing that I had already refined my skills to bypass antivirus software and web protections on both Safari and Chrome.
Relying on his trust in the system, I exploited his overconfidence and sent him a whatsapp message containing the phishing link disguised as a TikTok video he would find amusing—featuring a cat climbing a tree while chasing a mouse. The link redirected him to a fake TikTok login page that looked identical to the real one. Mr. Y, unsuspecting, entered his credentials, which my server quickly captured, and he was redirected to the funny video.

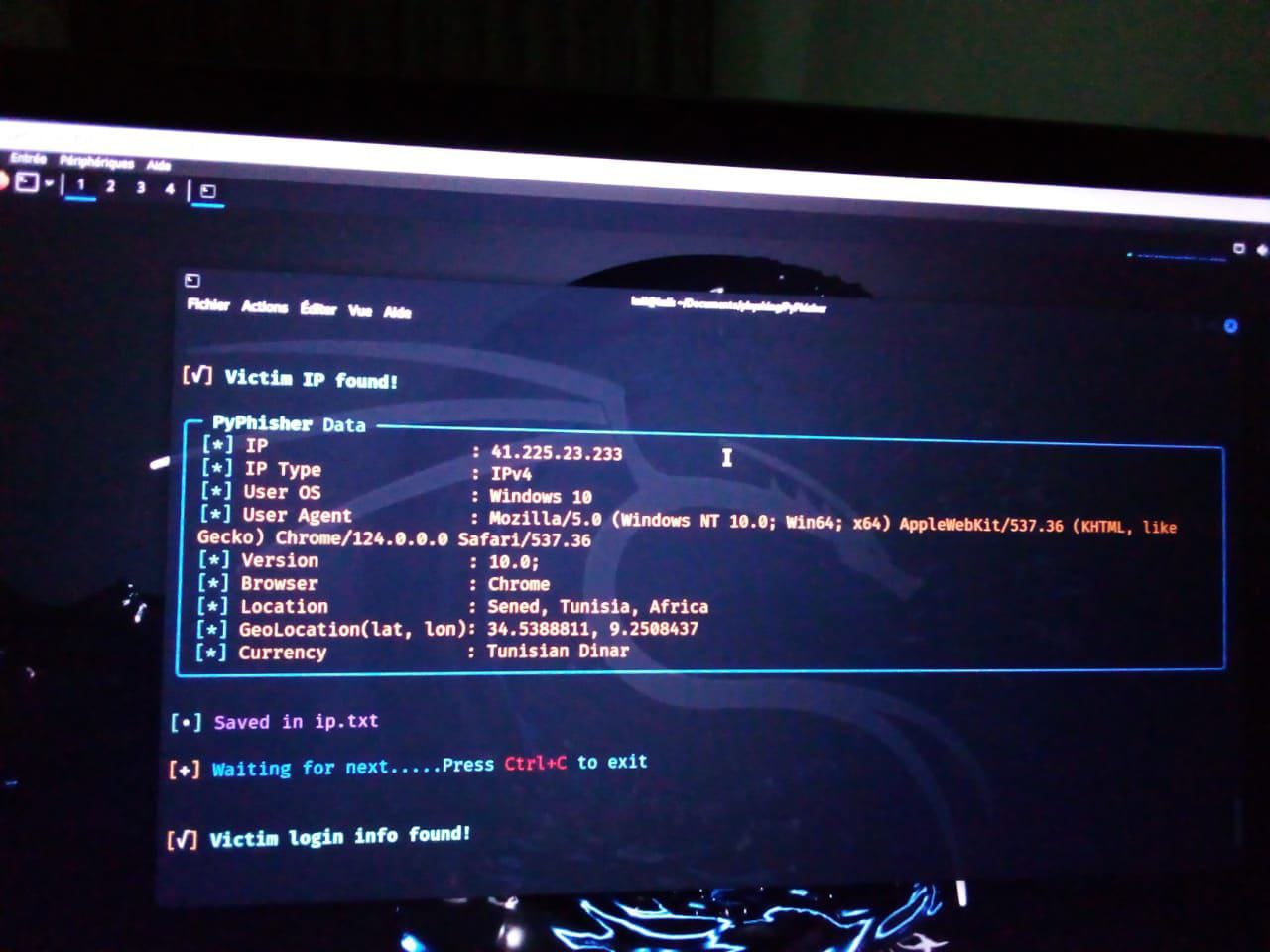
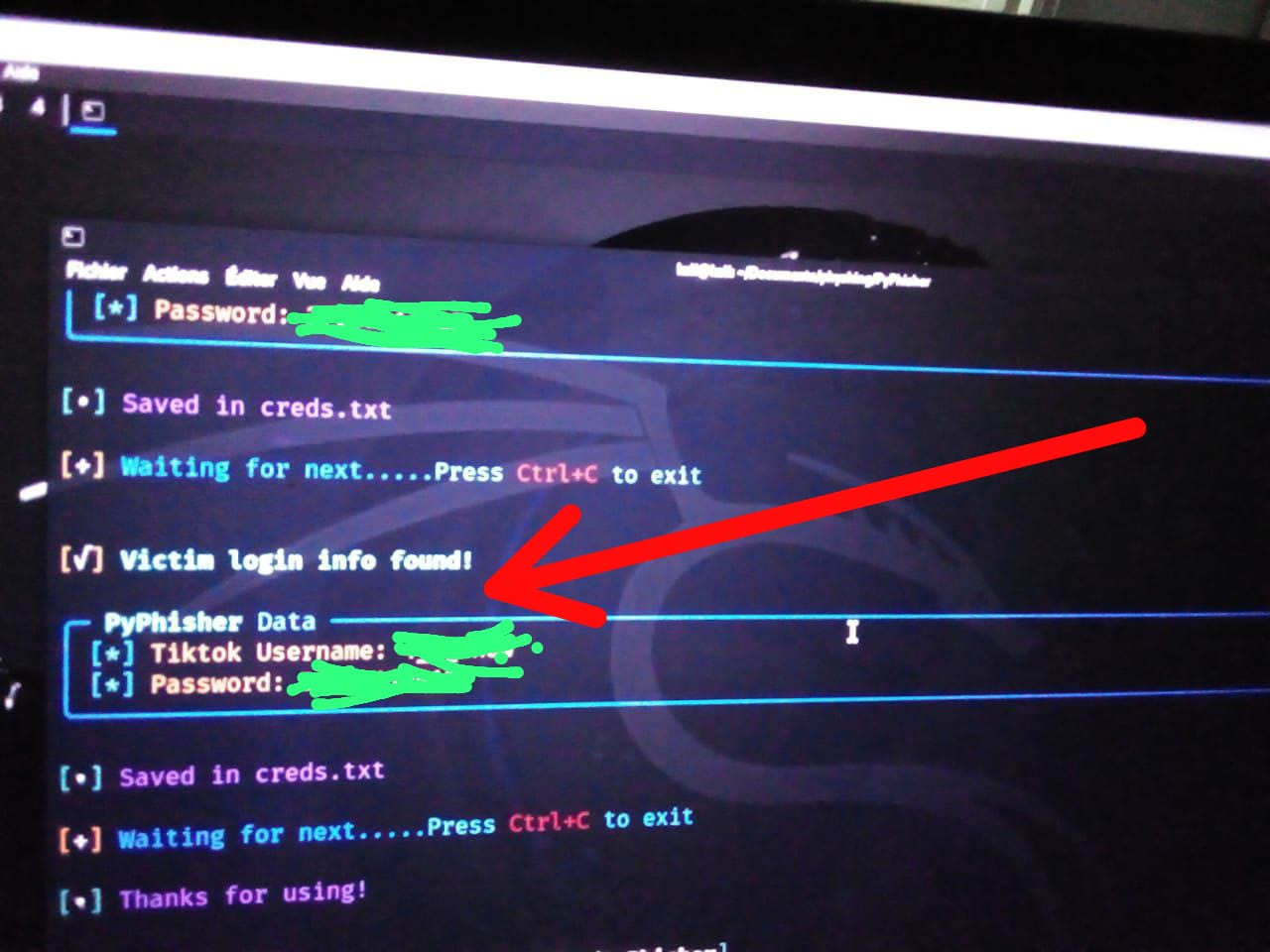
Dreaded Victory: Credentials Captured
As I sat on my bed, observing the real-time data flowing into my Kali console, I couldn’t help but laugh. Both Mr. X and Mr. Y had fallen for the phishing traps. I watched as their IP addresses connected to my server, and in an instant, their login details were mine. The game was over before they even realized they were playing.
"Captured Moment: The exact moment their login credentials were captured is displayed below."
Mr. Y even texted me about the cat video, saying, "Ohh, it's hilarious! The cat’s hungry, and the mouse doesn't want to die... hahahaha.", And I replied, "The poor cat... hahaha". He had no idea that his login information had already been compromised. He continued to joke. Meanwhile, Mr. X asked, "What a clever trick! Have you tried it?"
While I had the power to access their accounts, I knew the importance of privacy. I never peeked at their passwords. I simply captured the evidence I needed for the report, stored the data for my presentation, and prepared for the next phase of the project.
Screenshots Below : Phishing Messages & Fake Login Pages
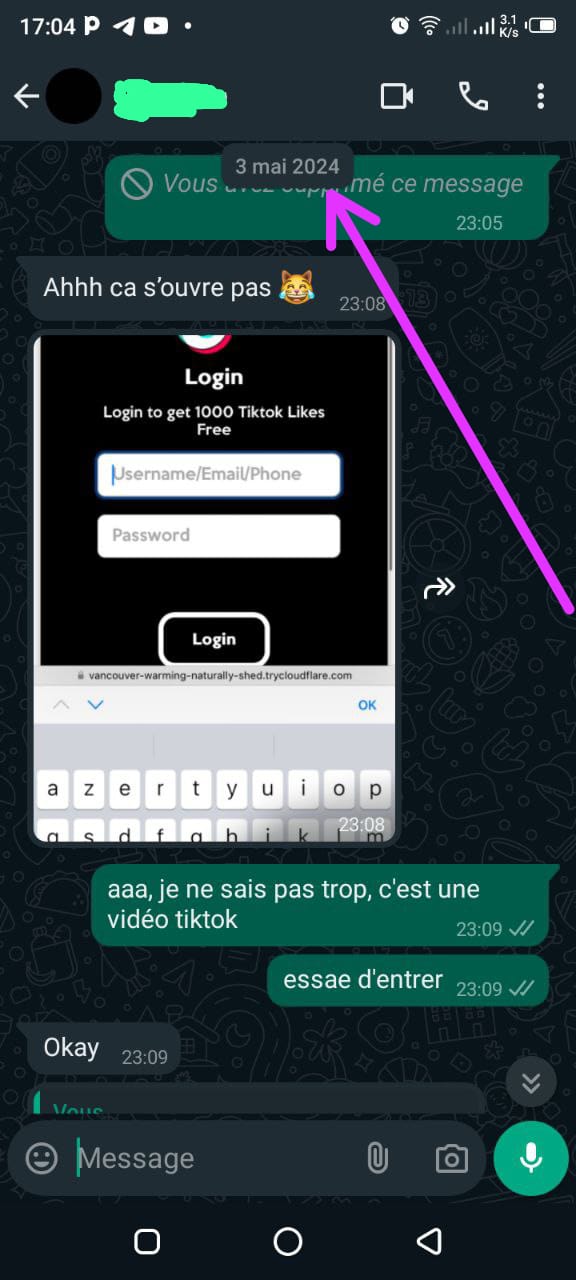
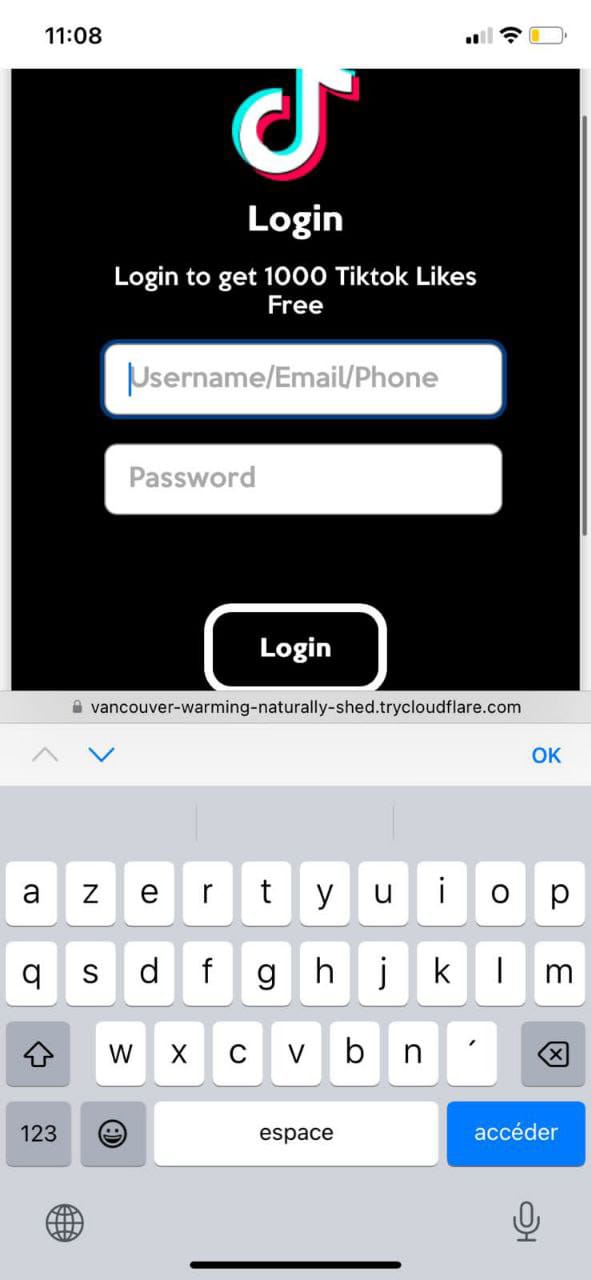
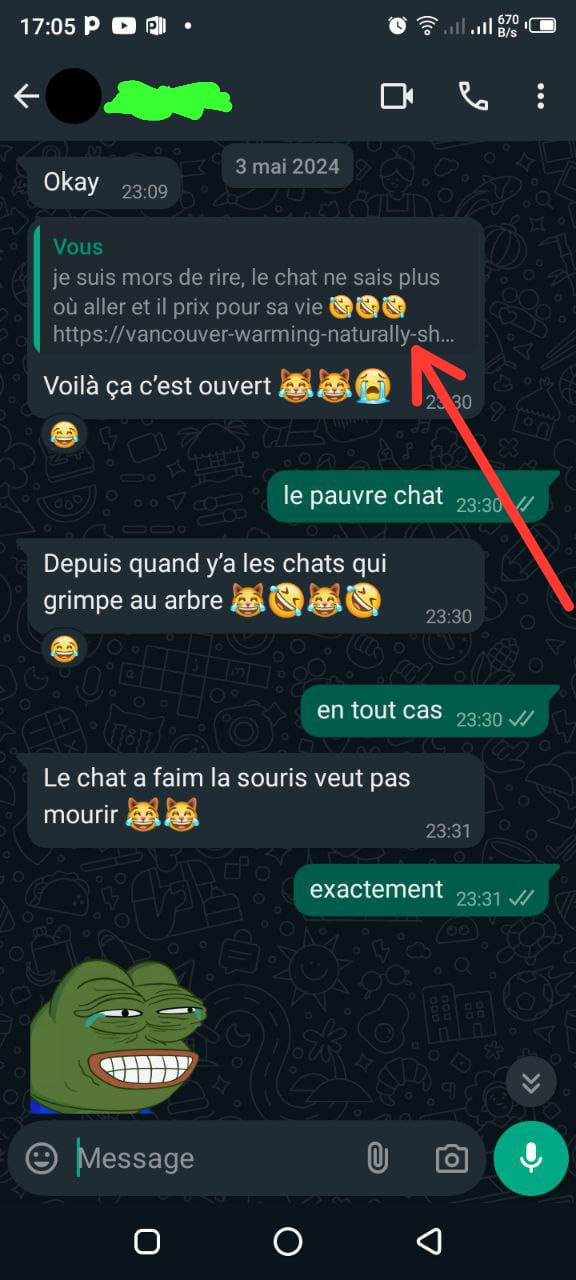

Screenshots Below : Capture Of Credentials

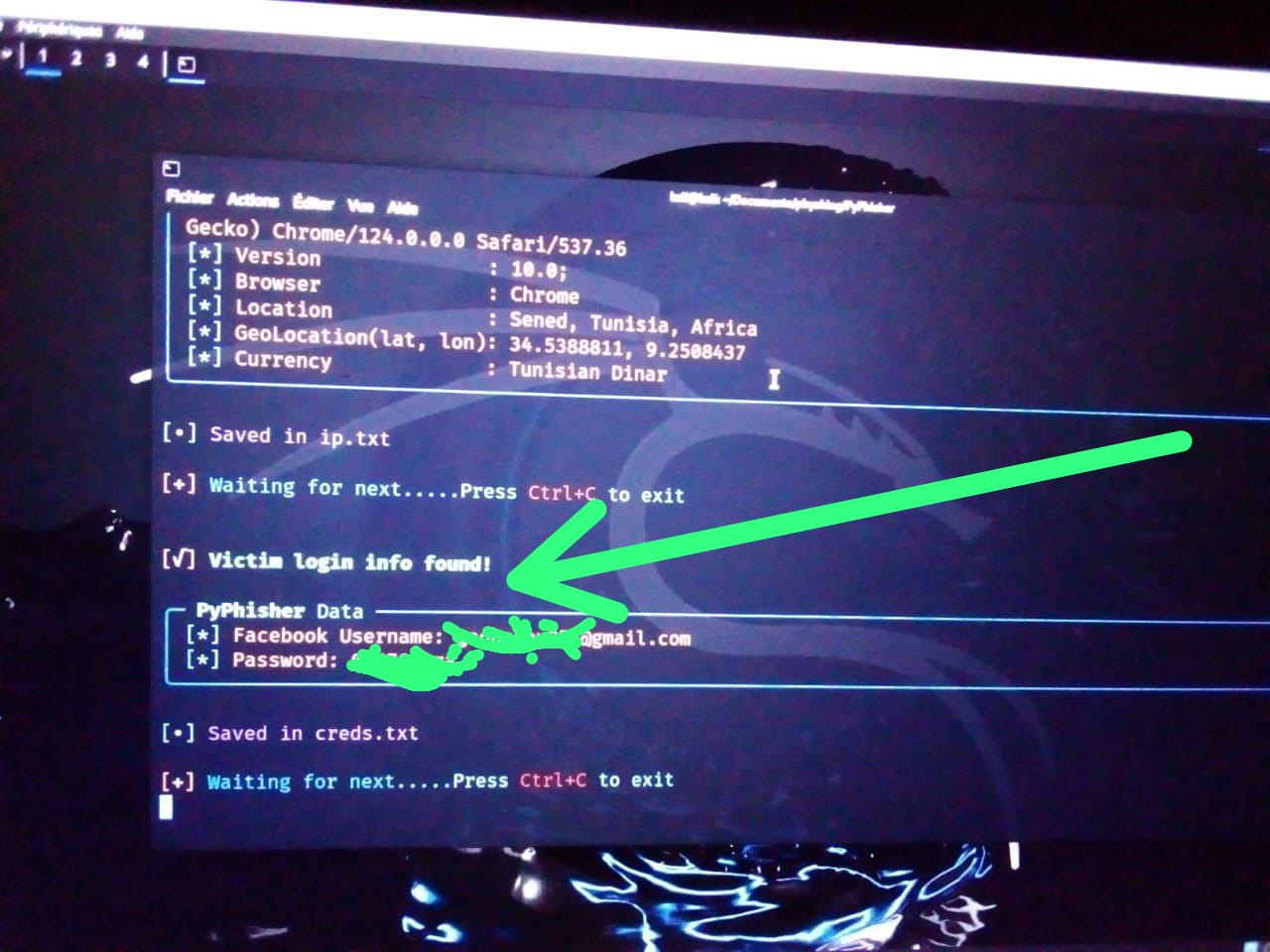
Step 4 : Maintaining Access & Privilege Escalation
Once I had obtained their login credentials, I moved on to the next phase : Maintaining Access. This step was crucial to demonstrate that I had successfully infiltrated their accounts. With full access to their profiles, I could clearly imagine the dangers this posed. A malicious hacker could have wreaked havoc by:
- Stealing personal data or sensitive information.
- Impersonating them online to scam friends or colleagues.
- Deleting or altering crucial information on their accounts.
- Spreading malicious links to infect others in their network. And More ...
In addition, I considered the possibility of escalating my privileges. For instance, I could attempt to access other related accounts, such as their Gmail accounts or banking services. However, I decided to keep things ethical and limited myself to testing their Gmail accounts. Fortunately, I discovered that they were using different passwords for their Gmail, which provided a small relief, they had at least followed one basic cybersecurity practice.
To prove my successful intrusion, I accessed their Facebook and TikTok accounts, and that's when the real fun began.

Mr. X's Facebook Account:
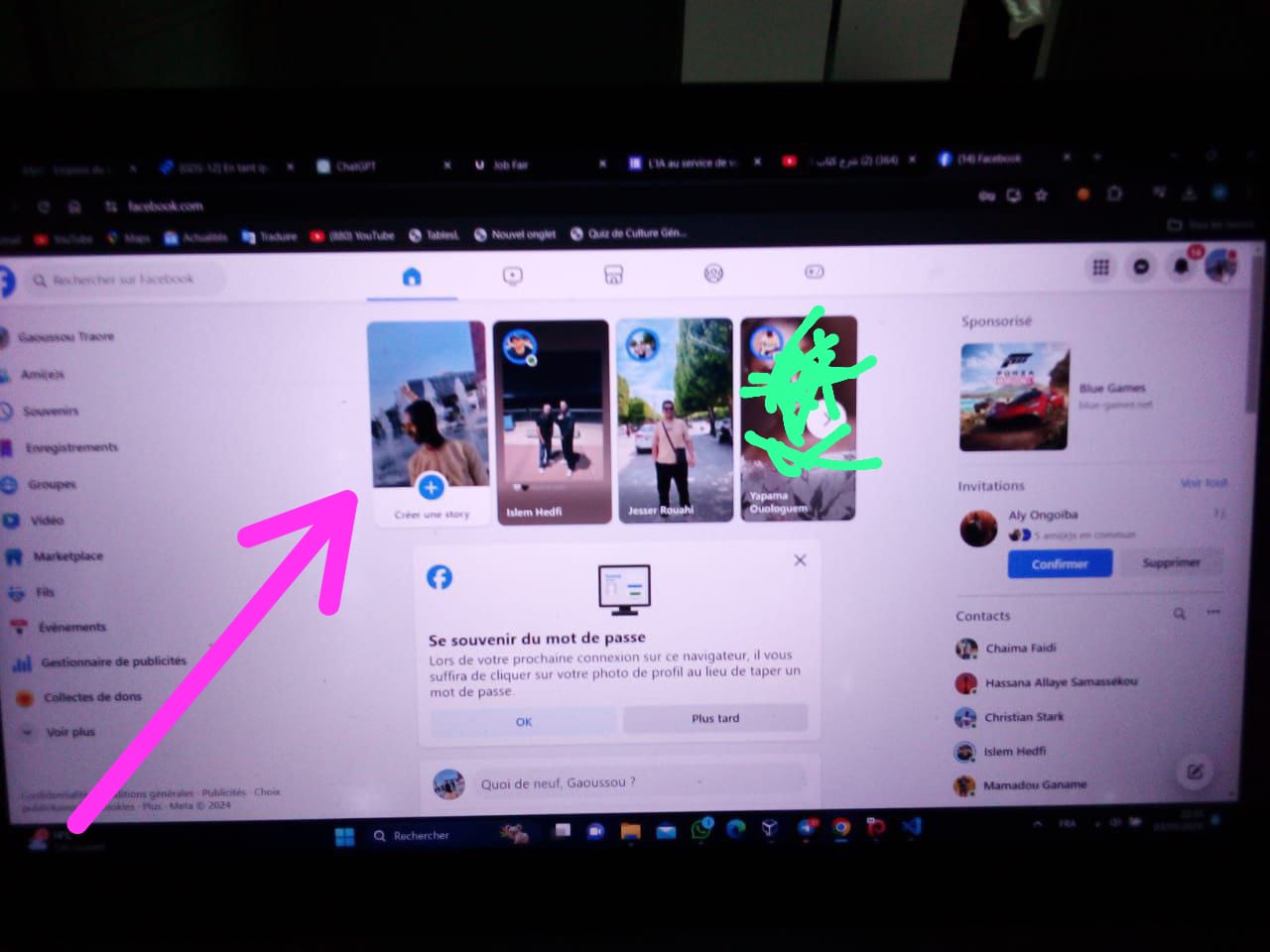
Once inside Mr. X's Facebook account, I decided to leave undeniable evidence of my access. I went to his story and posted the proof, but only made it visible to myself. I didn't want to raise any immediate suspicion from his friends, but I wanted to create a moment of tension. The stories I posted had a dramatic, almost eerie tone, to make him realize the seriousness of the situation.
For the first post, I used an image with the label 'You have been hacked!'. In the second post, I included the same message, but this time with a skull image to amplify the impact and add a touch of humor to the dramatic reveal. I thought it was amusing, but also a powerful reminder of how serious the situation could be if it had been a malicious hacker.
Not stopping there, I took it up a notch. I accessed his Facebook Messenger and sent a message from his own account to mine, pretending to be him. The message asked for urgent financial assistance. This was my way of showing just how easy it would be for someone with bad intentions to exploit his account and trick his contacts. Below are the screenshots proving the access and actions taken.

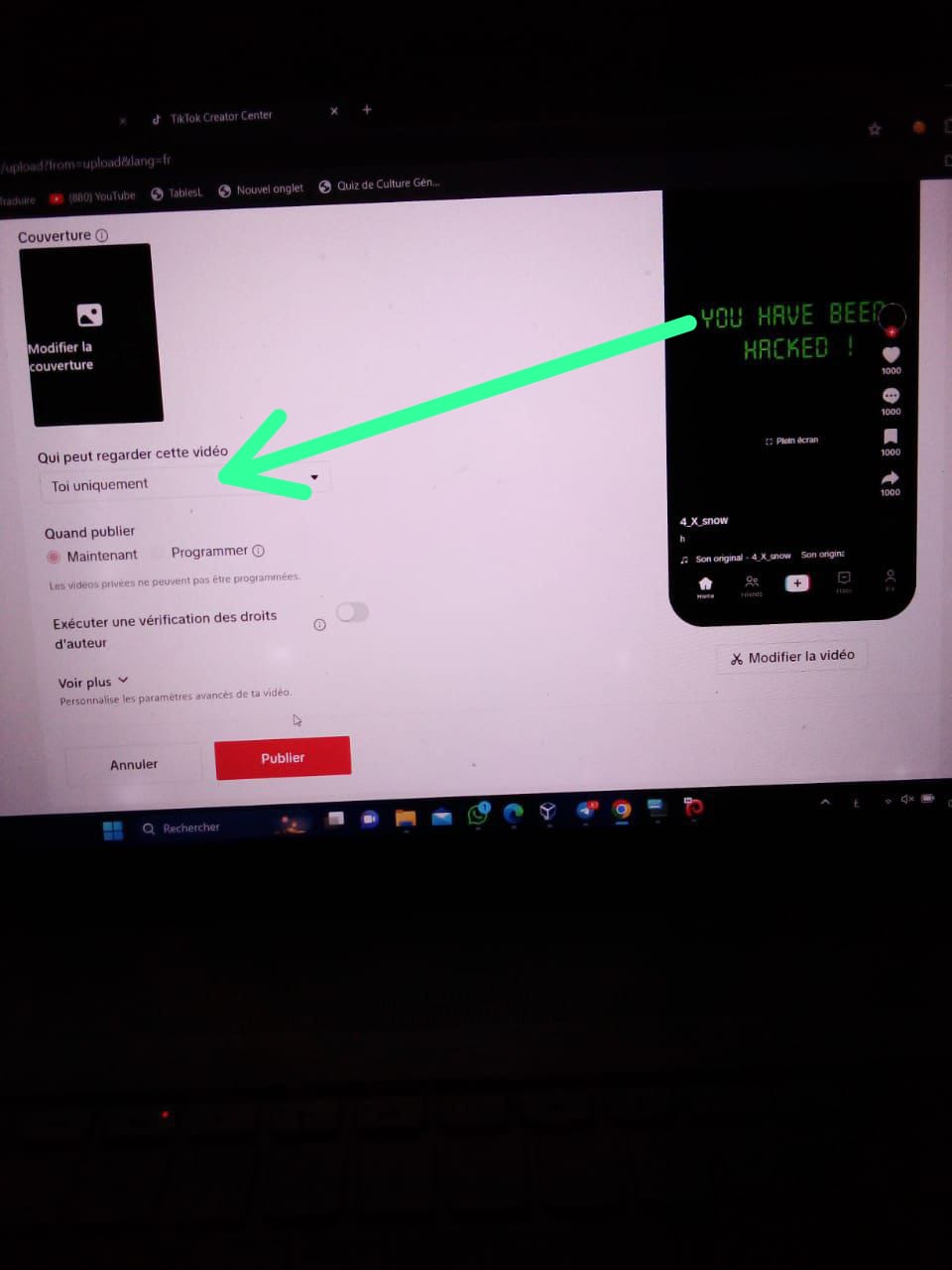
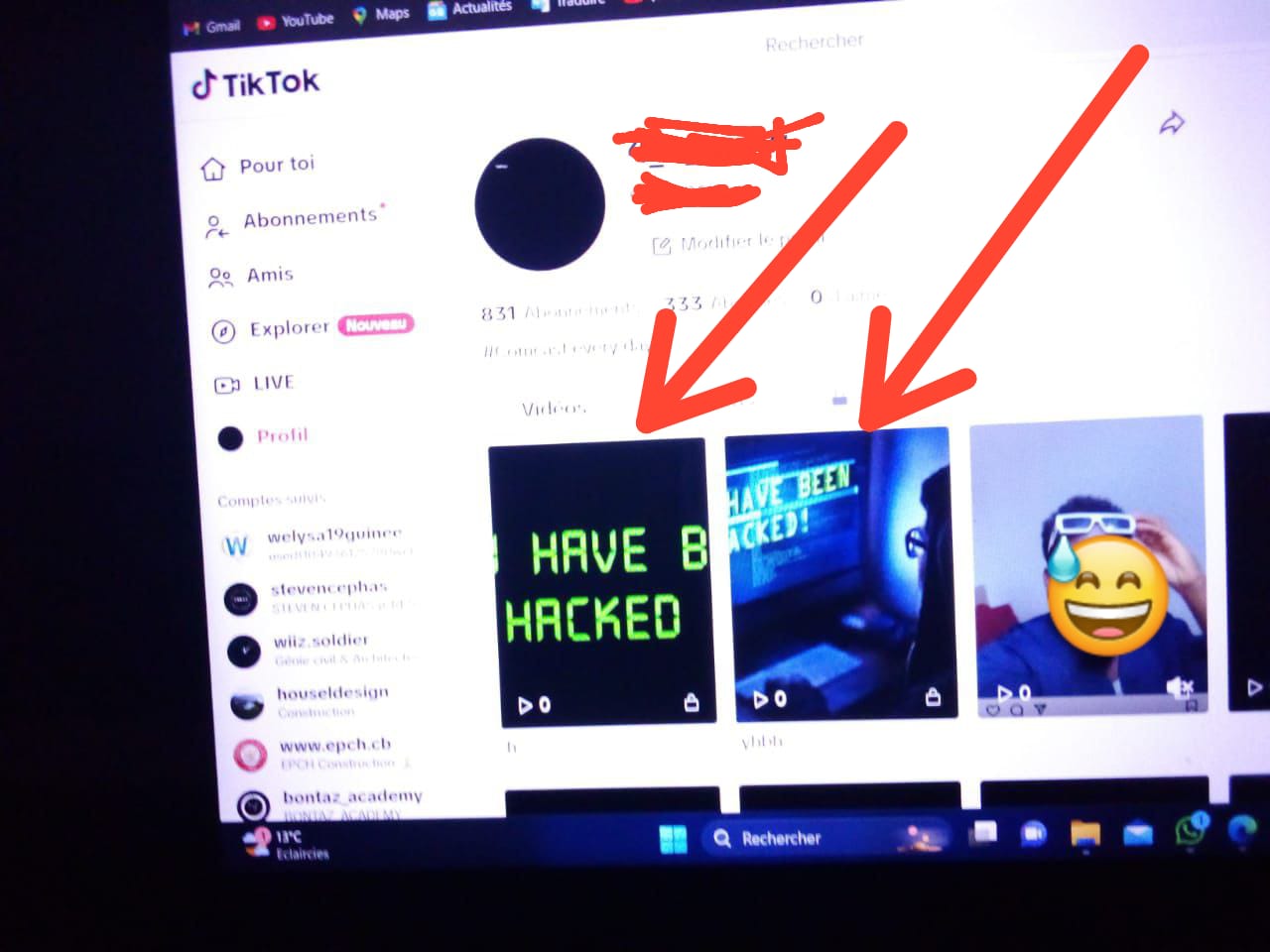
Mr. Y's TikTok Account:
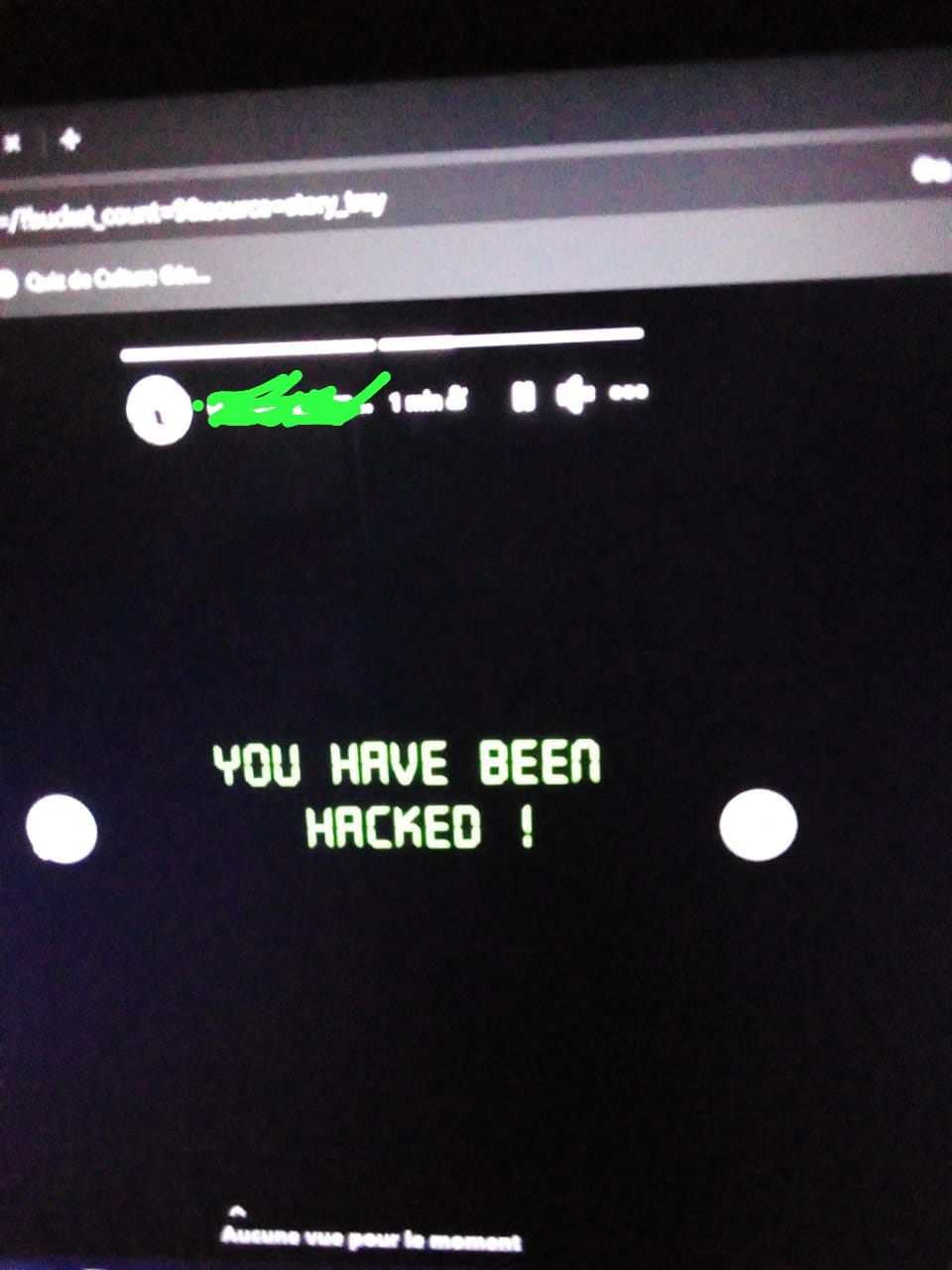
With Mr. Y, I followed a similar pattern. After accessing his TikTok account, I went to his profile and posted the same two images as I had done on Mr. X’s Facebook story. However, I made sure that the posts were visible only to him, ensuring it remained a private interaction between us, avoiding any public panic.
Just like Mr. X, the posts included the "You have been hacked!" message followed by the skull image. It was both funny and alarming. TikTok is an app Mr. Y spends a lot of time on, so I knew this subtle but clear warning would make him understand how vulnerable his data could be in the hands of a malicious hacker.
In both cases, I had full control of their accounts. From posting on their stories to accessing their private messages, the vulnerabilities were glaring. Had this been a real attack, their personal information could have been compromised in ways they couldn't imagine.
Mr. X's Facebook Account Takeover: Proof of Successful Intrusion



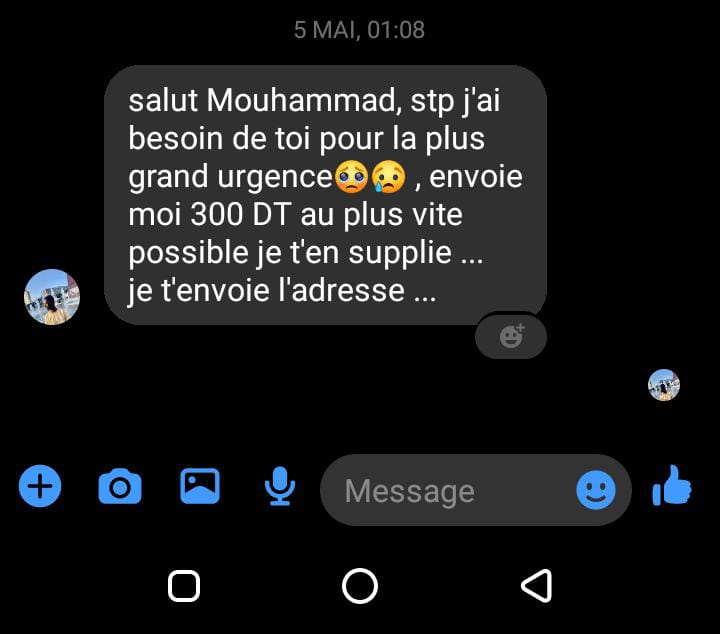
Mr. Y's TikTok Account Compromised: Demonstrating Full Control

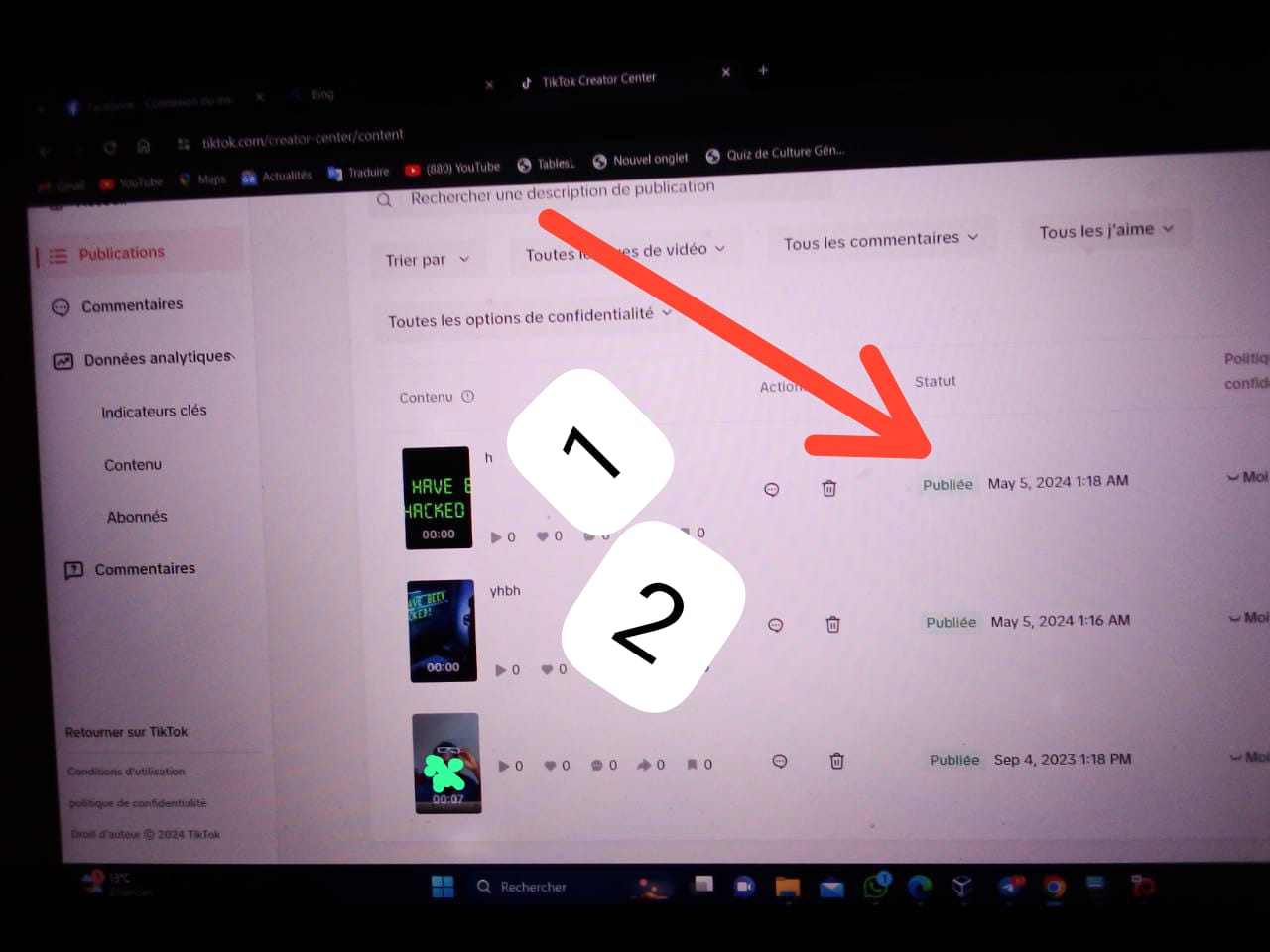
Step 5: Covering My Tracks
Once I had left undeniable proof of intrusion on both accounts, it was time to move to the next phase : covering my tracks and trying to act as if I was innocent. The first step was to delete the phishing links and messages I had sent to Mr. X and Mr. Y. However, there was still one potential trail that could expose my actions : the browser history, which could lead them right back to the phishing link and the vidéo. I decided to limit my activity at this point and not erase the browser history, opting instead to focus on the next stage.
The Revelation : Breaking the News
After completing all five steps, it was finally time to reveal what had happened. Now, the most entertaining part was about to begin! Both Mr. X and Mr. Y had no idea they had been hacked. Their blissful ignorance made the anticipation even more exciting. I went into the living room where they were casually sitting, completely unaware, ready to unveil the truth.

Mr. X's Shock
I approached Mr. X first, trying hard to suppress my grin. In a concerned tone, I asked, "Hey, Mr. X, what’s going on? Why are you asking me for money like that?"
He blinked, clearly confused. "Money? What money?"
Feigning worry, I pulled out my phone and showed him his Facebook story. "Oh, and what’s with this crazy story you just posted?"
He leaned closer, and BOOM! the words appeared on the screen, "You have been hacked!"
I dramatically dropped my phone onto the couch, letting the suspense build. Mr. X, now in shock, grabbed his phone to check it himself. His eyes widened as he saw the same message, followed by the skull. His voice trembled, "W-what is this?"
I couldn’t hold back anymore, bursting into laughter while Mr. Y joined in. "Looks like the Chinese hackers got you, Mr. X!" I teased.
Totally panicked and shocked, he stammered, "How... how did this happen?" We laughed harder, asking, "Who did you give your password to?" while still teasing him about his "serious" security breach. Mr. Y, still unaware of his own fate, laughed along with me, enjoying Mr. X’s misery.

Mr. Y's Realization
Now, it was time to shift focus to Mr. Y. I turned to him and said with a grin, "You’ve got that fancy iPhone, right? I bet no one can hack you!"
He smirked, feeling superior. "Yeah, man, iPhones are high quality. Mr. X should’ve gotten one!"
"Why don’t you check your TikTok account real quick, just in case?" I suggested. Confidently, Mr. Y opened his TikTok and within seconds... he saw it—the same dreaded message, "You have been hacked!" followed by the skull. His face dropped.
"No way... This is impossible!" he yelled, pacing around in disbelief.
"Yeah, yeah, yeah... impossible," I mocked him, while Mr. X, now back in the game, started laughing at Mr. Y’s reaction. We both found it hilarious, but Mr. Y stood there in shock, repeating over and over, "This can’t be happening...", "Yeah, .. You have been hacked!..." as he stared at the two images. I was nearly crying from laughter at this point.

The Accusation: “It Was You, Massoud!”
As the realization sank in, both Mr. X and Mr. Y turned to me and accused, "It was YOU, Massoud! Admit it, you hacked us!"
They started piecing it together. After a few moments of reflection, Mr. X exclaimed, "Wait! I remember now! You sent me that Facebook video about saving battery life recently."
"And you," Mr. Y chimed in, "sent me that funny TikTok video of the cat chasing the mouse up a tree!"
Both of them looked at each other, certain that I was the hacker. I denied it, saying, "You can’t just accuse me without proof!"
They then tried to prove it by going through my WhatsApp messages to find the links, but of course, I had already deleted them. That’s when Mr. X had the idea to check his browser history. He found the original Facebook video, but I pushed back, "Just because you see the video doesn’t mean it was me who sent it!"
In the end, we laughed it off, as the whole event was designed to simulate a real-world attack. That night, we laughed so hard that it became one of the funniest moments we shared.
Final Step 6: Reporting - Sharing the Proof & Raising Security Awareness
Once the fun settled down, it was time to shift to the most critical aspect of my project : the Security Awareness session. After sending both Mr. X and Mr. Y all the screenshots of their compromised accounts (you can see the captures below), I transitioned into the final phase: educating them on how they could prevent such attacks in the future.
This part wasn't just important; it was the core purpose of the entire project. The ultimate goal wasn't just to show that I could hack their accounts, but to raise awareness about the vulnerabilities they unknowingly exposed themselves to. Cybersecurity awareness is the most powerful tool against social engineering attacks, and I was determined to ensure they understood this.
We sat together for hours, from 1:00 AM until 4:00 AM, during which I walked them through various techniques they could use to protect themselves better. From enabling two-factor authentication (2FA) to understanding phishing risks, we covered a wide range of essential topics.
For a deeper dive into how I conduct these sessions and what was discussed in detail, you can explore my second project by clicking the button below:
Screenshots Below: With Mr. X
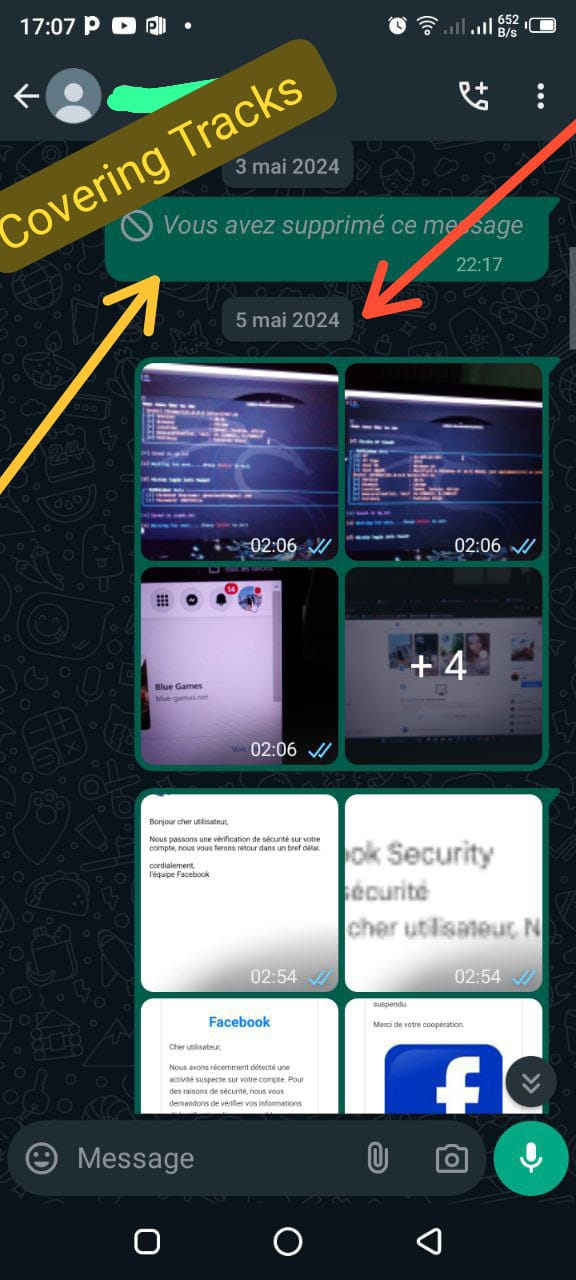
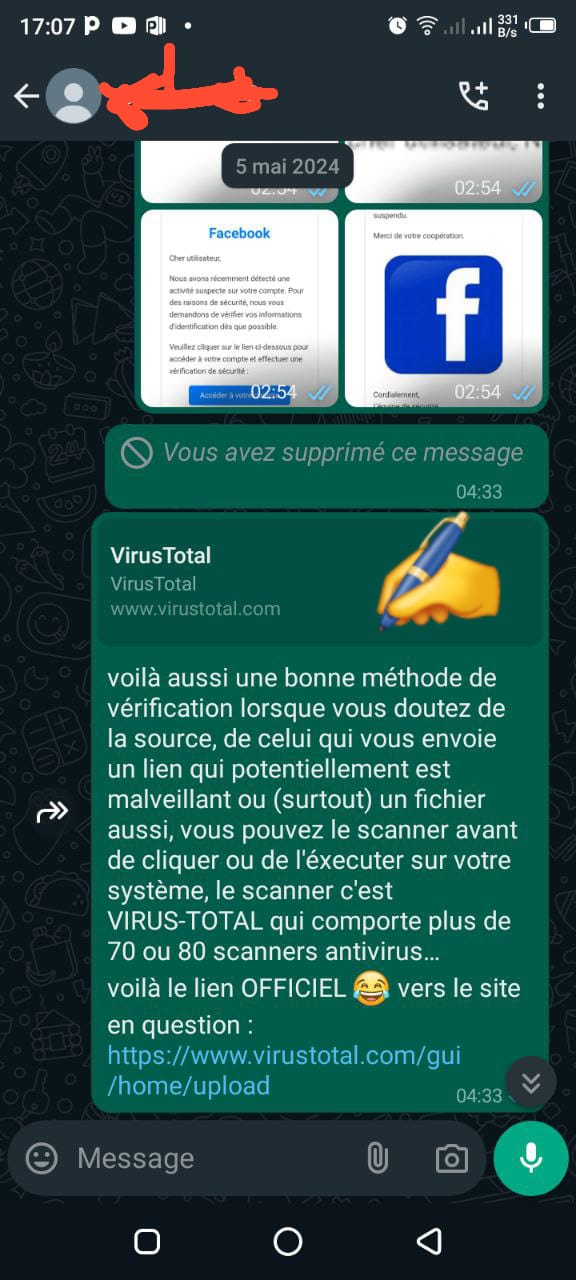
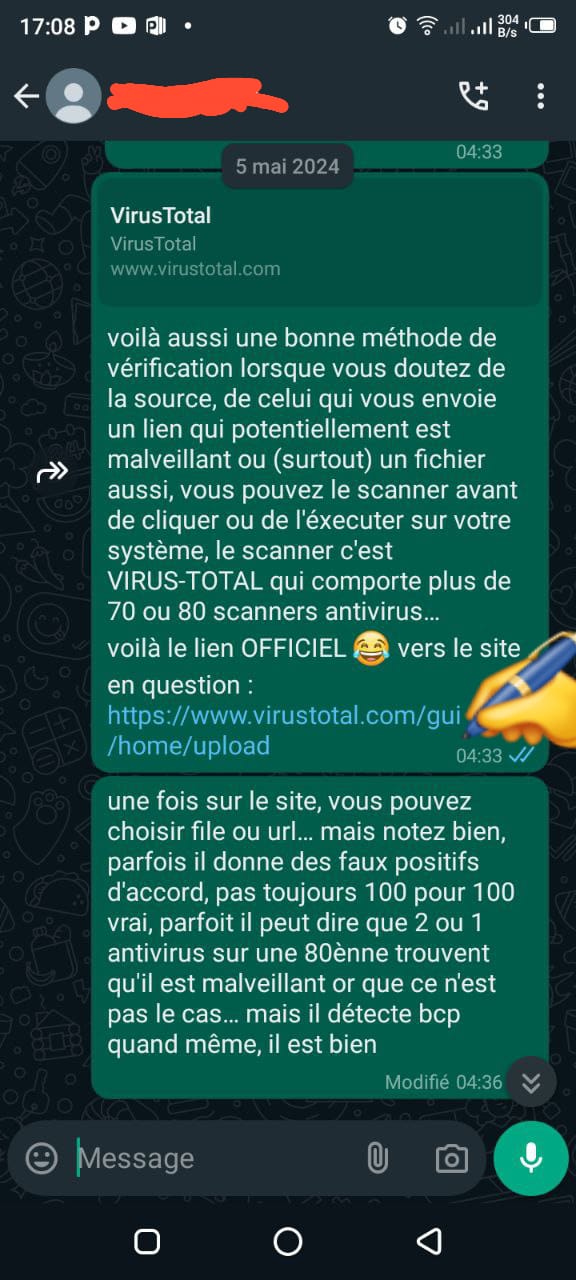
Screenshots Below: With Mr. Y
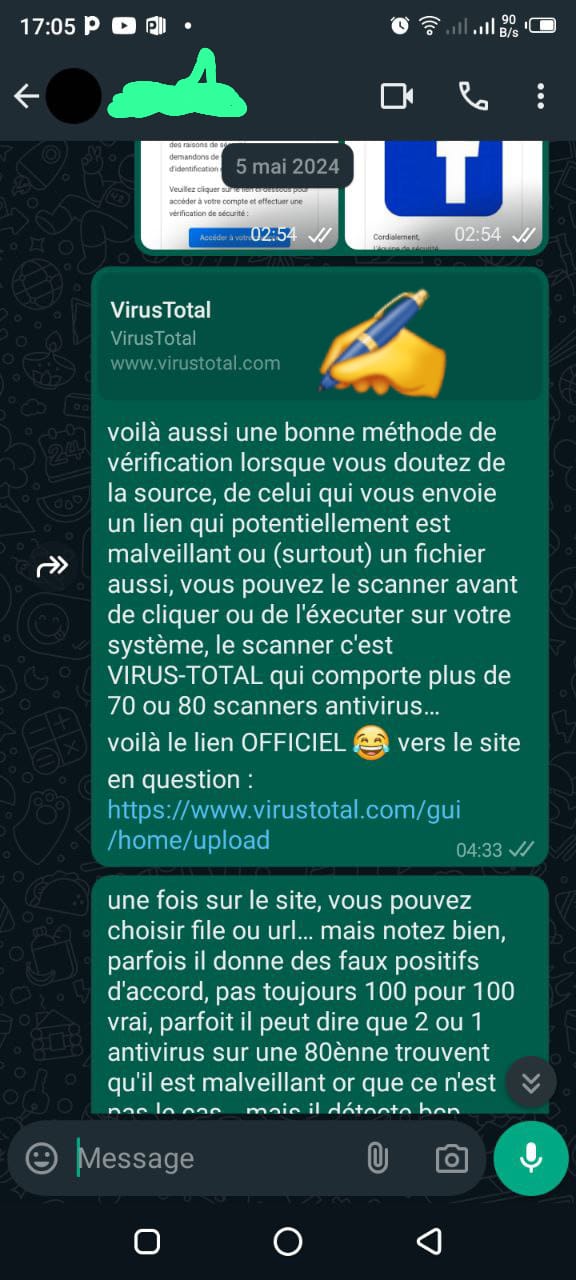
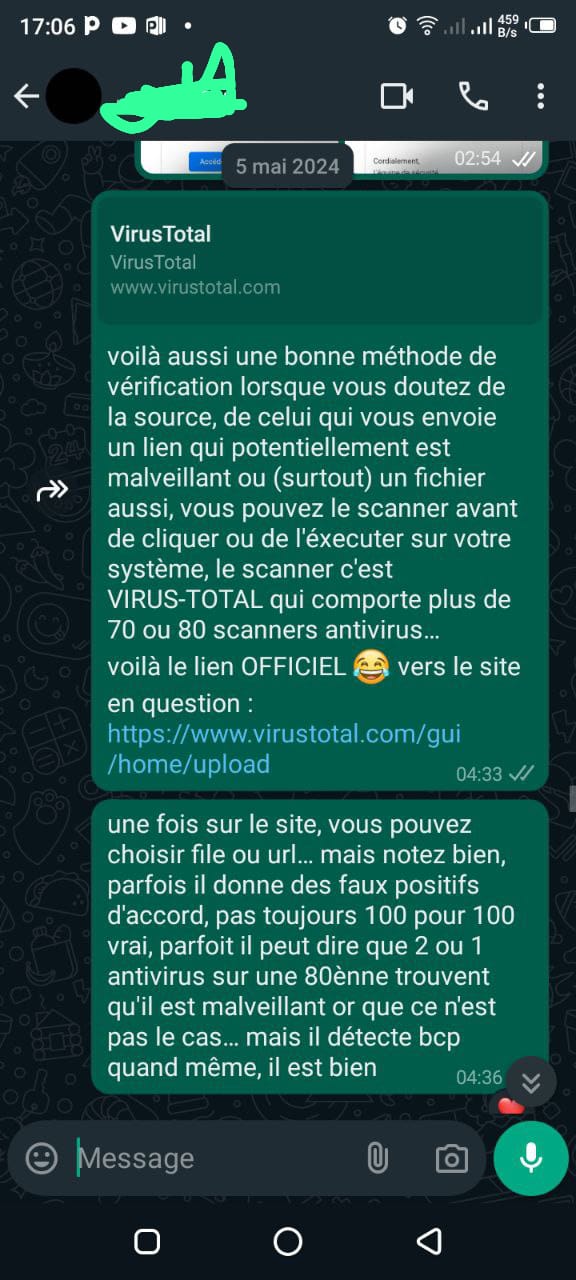

Lessons Learned & Strengthening Defenses
This ethical hacking project was more than just a demonstration of technical prowess—it was a crucial lesson in cybersecurity awareness. Through these steps, I was able to highlight how easy it can be to fall victim to cyberattacks, but more importantly, how to prevent them. Mr. X and Mr. Y's reactions showed just how eye-opening this experience can be when the reality of compromised accounts becomes clear.
From phishing vulnerabilities to a lack of two-factor authentication, these examples illustrate common weak points in personal online security. The key takeaway? Prevention is always better than reaction. By implementing simple, yet effective measures such as strong passwords and multi-factor authentication, these types of attacks can often be thwarted before they begin, or at least made much harder to execute, considering there are also methods to bypass 2FA.
This project underlines the importance of cybersecurity education. As the digital landscape evolves, so must our defenses—learning, adapting, and becoming more vigilant with each step.

